Mobile computing
- The process of computation on a mobile device is known as mobile computing.
- A set of distributed computing systems or service provider servers participate, connect, in mobile computing, and synchronize through mobile communication protocols.
- It provides decentralized (distributed) computations on diversified devices, systems, and networks, which are mobile, synchronized, and interconnected via mobile communication standards and protocols.
- Mobile device is not restricted to just one application alone, such as, voice communication.
- Offers mobility as well as stability with computing power.
- Facilitates a large number of applications on a single device.
Ubiquitous computing
- Refers to the blending of computing devices with environmental objects.
- A term that describes integration of computers with all objects in our everyday environment, endowing them with computing abilities.
- Based on pervasive computing.
Pervasive computing
- Pervasive computing is another term for mobile computing. When a set of computing devices, systems, or networks have the characteristics like transparency, application-oriented adaptation, and have an environment sensing ability.
- Transparency - Without the impact of location due to mobility, the access protocol deployed software or hardware component fails.
- Adaptability - Adaptability to the environment.
- Environment - Present location, surrounding devices and computing systems, present data, and available network, hardware or software components.
- Pervasive tends to mean ‘existing in all parts of a place or thing’.
- The next generation of computing takes account of the environment in which information and communication technology is used everywhere, by everyone, and at all times.
- Perceptive information and communication technology are the integrated parts of all facets of our environment like toys, computers, cars, homes, factories, and work-areas.
- Takes into account the use of the integrated processors, sensors, and actuators connected through high-speed networks and combined with new devices for viewing and display.
- Pervasive computing devices.
- Are not PCs.
- Are hand held, very tiny, or even invisible devices which are either mobile or embedded in almost any type of object.
Novel applications
- Mobile computing systems have a large number of applications.
- It has very recently made mobile TV realizable (The ultra-mobile PC unveiled in March 2006 has the size of a paperback book.)
- Some of the recent novel applications of mobile computing are:
- Smart phones.
- Enterprise solutions.
- Music, video and ebooks.
- Mobile commerce.
- Mobile cheque.
- Mobile based supply chain management.
SmartPhones
- A mobile phone with additional computing functions so as to enable multiple applications as given below:
- SMS (short message service), MMS (multimedia messaging service), phone, e-mail, address book, web browsing, calendar, task-to-do list, pad for memos.
- Compatibility with popular Personal Information Management (PIM) software.
- Integrated attachment viewing.
- SureType keyboard technology with QWERTY-style layout.
- Dedicated Send and End keys.
- Bluetooth capability for hands-free talking via headset, ear buds, and car kits.
- EvDO* support enabling the device as a wireless modem use for laptop or PC.
- Speaker phone.
- Polyphonic ring tones.
- 64 MB memory.
- Bright, high-resolution display, supporting over 65,000 colors.
- eMail, Wi-Fi, GPS, Web Browser, Live TV.
- Example of features on a recent Smartphone:

Enterprise solutions
- Enterprises or large business networks have huge database and documentation requirements to store it for future references.
- Refers to business solutions for corporations or enterprises.
- This may include specialized hardware or software programming to help in managing ontents with respect to:
- Storage.
- Security.
- Revision.
- Control.
- Retrievale.
- Distribution.
- Preservation.
- Destruction of documents.
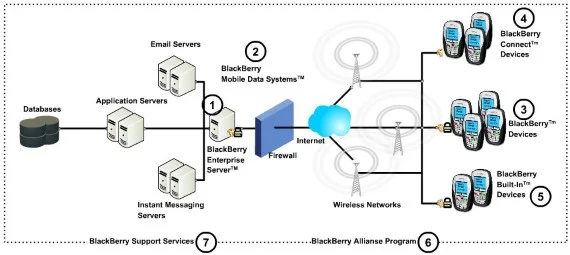
- An enterprise solution architecture for a BlackBerry device.
- It gives access to enterprise employees and connects to an enterprise server.
- It provides the company mobile users with a secure wireless access to their enterprise email and other critical business applications.
Mobile computing application to music and video
- Example─ Apple iPods enables listening to one’s favourite tunes anytime and anywhere.
- View photo albums.
- Slide shows.
- Video clips.
Mobile cheque
- It is a mobile based payment system.
- It is activated through text message exchanged among the customer, a designated retail outlet and the mobile service provider.
- Service provider authenticates the customer and activates the customer account in order to transfer money to the retailer account.
- Customers need not carry credit cards in their wallets for shopping anymore.
Mobile commerce
- Stock quotes in real time or on demand.
- Stock purchase or selling of the stock.
- Bank transactions.
- Retail purchases.
- Supply chain management.
- e-Ticketing─ booking cinema, train, flight, and bus tickets.
- Mobile-based supply chain management is used by the sales force and manufacturing units.
Limitations of mobile computing
- Resource constraints: Need for battery and recharging aspects is rich.
- Interference: In wireless signals, it affects the quality of service (QoS).
- Bandwidth: Due to the limited spectrum availability, it causes connection latency.
- Dynamic changes in communication environment: Link gets delayed and connection losses due to the variations and instability in signal power within a region.
- Network Issues: Network issues related to discovery of the connection service to destination and connection stability set as a limitation.
- Interoperability issues: It varies in the protocol standards.
- Security constraints: Protocols conserving privacy of communication may be violated. Physical damage/loss of mobile device is more probable.
Programming Languages
- Programming languages used in Mobile computing architecture are:
- Java: Platform independence - Program codes written in Java are independent of the CPU and OS used in a system due to standard compilation into byte codes.
- Java-J2SE: Has 2 limited memory sized editions - J2ME (Java2 Micro edition) and JavaCard (Java for smart card). It is widely used for developing language applications for a mobile device platform.
- The Java enterprise edition (J2EE): It is used for web and enterprise server based applications of mobile services.
- C and C++: Program compilation depends on the CPU and OS used. In-line assembly code can be used directly. It also provideses compact machine specific codes.
- Visual C++ and Visual Basic: Used for pocket PCs with Windows platform.
- Dot net (.Net): Widely used framework for mobile application development.
- Python 2.7: Popular platform for mobile applications.
Operating systems
- An Operating System (OS) enables the user to run an application without considering the hardware specifications and functionalities.
- Provides functions which are used for scheduling the multiple tasks in a system.
- Provides Management functions (such as creation, activation, deletion, suspension, and delay) for tasks and memory.
- Provides the functions required for the synchronization of multiple tasks in the system.
- Multiple threads synchronization and priority allocation.
- Provides Interfaces for communication among software components at the application layer, middleware layers, and hardware devices.
- Facilitates execution of software components on diversified hardware.
- Offers configurable libraries for the GUI (graphic user interface) in the device.
- Gives user application’s GUIs, VUI (voice user interface) components, and phone API.
- Renders the device drivers for the keyboard, display, USB, and other devices.
- Gives way for the development of middleware, applications and new application environment.
- Some of the popular operating systems used in mobile computing are Symbian OS, Windows CE and PalmOS.
Middleware for mobile systems
- As Middleware is the Software components, it links the application components with the network-distributed components.
- Mobile OS also provides middleware components.
- A few examples of middleware applications are:
- To discover the nearby device such as Bluetooth.
- To discover the nearby hotspot.
- For achieving device synchronization with the server or an enterprise server.
- For retrieving data (which may be in Oracle or DB2) from a network database.
- For service discovery.
- For adaptation of the application to the platform and service availability.
Mobile computing architectural layers
- Defines various layers between the user applications, interfaces, devices and network hardware.
- A well defined architecture is necessary for systematic computations and access to data and software objects in the layers.
- Interaction of two adjacent layers takes place through input-output interfacing.
- An application deploys the software components and APIs (Application Program Interface) at Application layer.
- The Client APIs can be considered as the top most layer in the architecture.
- There are middleware components which discover the service, do the linkage between the client and network service, update database, manage the device using remote-server software, perform client-server synchronisation and adapt the application to the given platform and server.
- OS is a layer in between the application and hardware. It facilitates the running of the program, hiding the specifications of the hardware and provides many OS functions (example: Device drivers).

Protocols
- Interchanging two diversified and distributed components need protocols and standards.
- Mobile computing services use a number of mobile communication protocols such as
- CDMA.
- WCDMA.
- HSPA.
- UMTS, and I-Mode.
- LTE and WiMax.
- WPAN protocols─ Bluetooth, IrDA, and Zigbee.
- WLAN protocols ─for example, 802.11a and 802.11b.
- WAP (Wireless Application Protocol).
Mobile computing architecture - layers
- There are different layers in network transmission and reception or in the interchange of information.
- The OSI (Open Standard for Interchange) Seven-layer format is listed below:
- Physical for sending and receiving signals (for example, TDMA or CDMA coding).
- Data-link (for example, multiplexing).
- Networking (for linking to the destination).
- Wireless transport layer security (for establishing end-to-end connectivity).
- Wireless transaction protocol.
- Wireless session protocol.
- Wireless application environment (for running a web application, example, mobile e-business).
Mobile Smartphones, Smart mobiles and Systems
- Communicate with other phones using a cellular service-provider network.
- Loaded with smart functions and are available in smaller sizes.
- Applications of mobile phones are no longer confined to telephonic communication alone. It has eliminated and over thrown the application of telephonic communication.
- Can synchronize, upload and download data to and from PCs.
- Provides e-mail and Internet connectivity.
- Click pictures and prepare albums.
- Includes a personal information manager (PIM), a handheld computer, and an entertainment device.
- Pack in everything from a computer to an FM radio and from video recording to TV viewing.
Broad categorization of mobile devices
- Smart phones: Hybrid cellular phones possess some advanced functionalities of multi phones or multimedia phones besides functioning of regular mobile phones.
- Smart cards: A mobile computer chip sandwiched within a very small space between the layers of the card is called as smart cards.
- Smart Sensors: Sensors in a mobile device enable it to interact better with its surroundings. Deployed smart sensors connect and convey essential information to mobile control systems.
Smartphones features
- A mobile smart phone is a handheld computing device offering the below features besides voice communication.
- A GSM, CDMA, or tri-band wireless radio interface to a cellular network provided by a mobile service provider.
- LCD display or Touch screen is another milestone in the feature of smart phones.
- A smart T9 keypad: T9 stands for ‘text on 9 keys’. A smart keypad is one that recalls previous entries of key. A text input system that offers an alternative to a QWERTY keyboard′s multi keys by multi-tapping the same key.
- Functions as a phone as well as a PIM (Personal Information Manager)for, like, phone contacts, address book, task-list, calculator, alarm, and calendar
- Ability to send and receive SMS messages.
- Ability to send and receive MMS (multimedia messaging service) messages for transmission of digital images, video clips, and animations.
- Data synchronisation for connecting mobile device to a PC.
- Provisions for games, e-commerce, and e-ticketing.
- Bluetooth communication with PCs and neighbouring devices.
- Integration of location information, GPS and maps.
- WAP, Wi-Fi or internet enabled for Web page access, download, and other Web-based applications through a WAP gateway or proxy or XHTML based page access.
Multimedia features in Smartphones
- Offers multimedia functionalities.
- Can play MP3 format audio and MP4 format video files (Some phones may also support other formats such as WMA, AAC, etc.).
- Provide enough amenities for cameras to do still pictures and video recording. Some phones extend their service by providing picture-editing software which enables the user to edit, crop, and refine pictures on their cell phone handsets.
- Possible to watch TV on a mobile phone using 3G HSPA/CDMA/EDGE/EGPRS connectivity.
- Many mobile service providers link up with various TV channels and enable users to enjoy mobile TV on the LCD screens of their cell phones.
- Mobile phone gaming enabling users to play networked multiplayer games.
Digital music players
- These players include software that play music files encoded in the formats of MP3, WMA, Realmedia etc on mobiles PCs and laptops.
- Use Flash memory. Capacity may vary from about 128 MB to over 80 GB.
- Present day media players enable video as well as audio playback.
- Apple iPod: Simple User interfaces and designed around a central scroll wheel. Uses Apple itunes software for transferring, storing, managing and playing music and videos and displaying photos. It also provides data synchronisation between iPod and PC.
Other features of mobile devices
- Bluetooth: Creates Personal Area Networks(PAN). Transfers data with high level security. Consists of 8 network devices in 1 Picocell. A Picocell can act within 10m distance. It is accepted for open wireless technology as per IEEE standards for exchanging data over short distances. Uses short wavelength radio transmissions in fixed and mobile devices.
- Wi-Fi : Supports data transfer at high speeds.
- GPS: Global Positioning system gets abbreviated as Geographical positioning system. Mobile systems can have a GPS receiver or can be provided the GPS location through its service provider. It helps in receiving signals from various GPS satellites orbiting earth.
- Gyroscope: Sensor besides measuring the change in velocity (Angular acceleration) changes in direction (angle) also. These measurements are used in Mobile gaming applications running on a smart device.
- Accelerometer: Sensor which detects linear acceleration along 3 axes X, Y and Z. Detects up/down, right/left and front/back acceleration given to the device by the user.
- Digital Compass: Shows directions North South East and West.
- Magnetometer: Enables 3 dimension interactions without any touch from nearby mobile device. Software monitors the changes in magnetic fields around the smart phone and identifies the users’ gestures.
- Camera: Provides auto-focus, Xenon or LED flash for pictures and videos.
- 2D and 3D Graphics and HDMI (High definition multimedia interface): HDMI is a compact audio/video interface used for transmitting digital data without compression.
Handheld pocket computers
- Pocket-sized PCs.
- Highly differ from smart phones and multimedia phones in the programming of customized applications.
- Offer a variety of application and programming tools those are not included in new generation mobile phones.
- Unlike smart phones, (use the text-on-nine-keys format), handheld computers have full text keypad or a touch screen keypad.
- Stylus generally used to enter data into handheld devices such as PDAs and palmtops.
- Some allow the user to write on the screen using a stylus and incorporate special software for handwriting recognition.
- Include word processors and spread sheet software as well as PIM software.
Handheld pocket computers differences with Laptop
- Pocket PCs do not have CD drives and hard disks.
- Use flash memory or microSD card.
- Allow the insertion of a memory stick (A memory stick is a removable flash memory card.).
- Clock speeds of pocket computer processors are limited up to 200 MHz due to consideration on battery life.
- Unlike laptops and notebooks, which use regular microcomputer operating systems, pocket computers have specially designed operating. systems scaled to the requirements of the software, hardware, and peripherals used in handheld computers like Windows CE, Windows 7, MAC OS 4 and Android.
Smart systems
- Have embedded computational devices. Provides comfort, efficiency and remote access to devices and appliances.
- Smart cards, labels and tokens are widely used in consumer goods and service industries.
- Sensors and actuators are electronic devices that make automated systems possible.
Smart cards
- Also known as integrated circuit cards (ICC).
- Small pocket sized cards with electronic processing circuits embedded.
- Some act as memory cards (for storing data).
- Can also have embedded microprocessor circuits.
- Do not have batteries. Energy is provided by card reader.
- Examples: Credit/Debit card, ID card, Access card, Library card.
Contact smart cards
- Have small gold coated pins on the chip which helps in providing contact with the electrical circuits of the card reader.
- Requires insertion into a smart card reader with a direct connection.
- Physical contact allows transmission of commands, data and card status to take place.
Contact-less cards
- Radio frequency (RF) induction technology is a main source for communicating with card reader. Have to be held close to the reader antenna.

Smart labels
- Have a processor, memory, transceiver and antenna like a contact-less smart card.
- Label differs from a card in terms of thickness and visibility.
- Powered by the received signals.
- Since wireless communication is used, label need not be visible when implanted into a product or package.
- Smart labels are networked together using a central reading or computational device (Host) or PC.
- Cluster of labels form a network similar to a LAN network.
RFID
- Automatic identification method for remote storage and retrieval of data on RFID tags.
- RFID tags are objects tagged on to people, products or animals to enable their identification using radio waves from a nearby source.
- Contains integrated circuit and antenna.
Smart tokens
- Tokens are used for authentication purposes before an action, such as granting entry into a restricted area.
- Smart token is an encapsulated circuit consisting of embedded processor and memory.
- Sizes are small, usually like a shirt button or pen nib.
- Uses either a wire based protocol or contact-less communication.
Sensors
- Electronic devices that sense the physical environment (temperature, pressure, light, etc.).
- May be a sophisticated set of tiny devices.
- Smart sensors are the sensors with processor and memory.
- They have computational, communication and networking capabilities.
- It consists of the sensing device processor, memory, analog to digital converter(ADC), signal processing element, wireless/infrared receiver and transmitter.
- Generally programmed using assembly language or C.
Actuators
- Receives commands or signals from a network, mobile device, computer or controller and accordingly activates the physical device/system.
- Sensor-actuator pairs are used in control systems.
Smart appliances
- With automation technology, it is possible to control home appliances and security systems using a cell phone or a computer.
- Appliances can be networked by using power lines which induce signals. These signals can be communicated from one appliance to another, forming a network.
- Devices can also communicate through a central server or a short range wireless protocol like blue-tooth or ZigBee.
- Can be web enabled devices connecting to the internet through a residential gateway.
- Can also be allotted a number by the mobile service provider which can be controlled using SMS service.
Set-top boxes
- A sophisticated computer based device.
- It has data, media and network processing capabilities.
- Interconnects the home TV and broadcasting service network.
- Java is the most commonly used programming language.
- Runs deciphering and encrypting software.
Limitations of mobile devices
- Mobile devices are limited in various ways such as
- Quality and security of service.
- Energy Constraints in Devices.
- Hardware Limitations.
Quality and security of service
- Technical restrictions and practical considerations make it difficult for service providers and device manufacturers to ensure that the mobile device operations run uninterrupted.
- Sustaining quality of service along with the provisioning of seamless access to all users.
- Some of the limitations with respect to quality and security are as follows.
- Accessibility :
- Since smart labels transmitted signals are low in power. Smart labels on packages have limited access.
- These labels can only be read within short ranges.
- RFID access is limited to ranges within line of sight.
- Range :
- Signal strength is inversely proportional to the square of the distance from the transmission source.
- There is also degradation of signal quality due to reflection, scattering and diffraction.
- Accessing mobile device is limited to the range of the signal strength resulting that it can be separated from the noise
- Security :
- Unsolicited advertisements and unwanted messages.
- Virus attacks.
- Hackers render it functionless or threaten integrity and security of the data stored on the device.
- Noise signals transmitted by an attacker can completely jam a mobile device.
- Repeated transmission of unwanted signals by an attacker can drain the resources of the device.
- Energy resources depleted fast when computations are forced and authentication algorithms are run repeatedly.
- Connectivity.
- Connectivity loss or intermittent connectivity do happen in certain situations.
- The atmospheric condition and changes in environment affect signal strength.
- In the event of heavy rain, there may be complete loss of connectivity.
- Mobility:
- Non-availability of an access point or base station.
- Infrastructural issues.
- No base stations or Wi-Fi hotspots providing connectivity and access to the Internet to sensors, labels, automotive systems, RFID tags, and cell phones.
- Use of different standards in different regions limits the operability.
- A GSM phone may not be operable in all continents hence hampering global roaming for the user.
- Some service providers may not be able to provide connectivity in all parts of the country or in other continents, etc.
Energy constraints in devices
- All mobile devices have limited energy stored in battery.
- Battery size and power limited due to considerations such as size, weight, and bulk of mobile devices.
- Due to the need of the devices to be recharged after some period, limits device mobility.
- Some devices such as smart cards, smart labels, remote sensors, and actuators do not even have a battery of their own.
- They derive their energy from the radiation received from a wireless source in vicinity.
- Such devices, therefore, require these sources to operate.
- Mobile Computing Strategy
- Processor circuit dissipates higher energy when its clock frequency is higher.
- Computational speed higher at higher clock frequency.
- A device is, therefore, programmed so that only computations such as graphic image processing run at full processor speed.
- The clock frequency reduced for the other computations to save power.
- The clock is activated only when a device interrupts or starts processing instructions.
- Many innovative mobile computing strategies adopted to mitigate the effects of energy constraints on mobile computing.
- Use ZigBee protocol─ a lesser stack size as compared to Bluetooth so less energy dissipation due to lesser computational requirements.
- When a host or hotspot seek certain data from a device frequently, program adapts itself so that the frequently required data is calculated and stored in a buffer from where it can be sent at slow clock frequencies on demand from the host.
- A program can also just transmit any changes in the data with respect to previous data.
- Communication scheduling strategies are adopted.
- Frequently required data transmitted as per schedule.
- This saves the host energy which would otherwise be required for sending commands and also saves the devices energy that would be dissipated in processing the commands .
- Processor Design:
- Innovative circuits of mobile device processors have been designed and are keeping on improved upon so that the same program instructions process with lesser energy dissipation per unit computational speed.
- Examples of energy efficient processors─ ARM and TigerSharc.
- Transceiver Design and Programming Strategy:
- Designed such that signals of just sufficient strengths transmitted to the receiver.
- Just sufficient strength means that the signal strength is low but clearly distinguishes noise and maintains message integrity.
- Control commands from the host are sent at lower signal frequencies.
- Once the device is ready and gets powered up, the transceiver transmits the data for operation.
- Multi-hop routing─ reduce the distance up to which a signal is required to travel.
Hardware limitations
- Besides Energy limitations due to battery size, all mobile devices face various hardware constraints too.
- Memory:
- Constraints on memory.
- Most mobile devices do not support hard disk drives and CD drives due to size limitations.
- Innovative forms of memory designed and are continuously improved upon.
- Internal flash drives and the card slots for external memory are used.
- Memory stick used to enhance the memory in the device.
- Bandwidth:
- Availability of bandwidth is limited by the frequency spectrum that a regulator allots to a service provider. A regulator regulates the frequency and signal strengths permitted.
- A service provider is not permitted to air signals at any random frequency and signal strength.
- The service must use the frequency spectrum allotted to it in an efficient manner.
- Multiplexing and coding techniques help in achieving efficient transmission.
- The technology in use also limits the spectrum efficiency. For example, CDMA has higher spectrum efficiency as compared to GSM.
- Limited bandwidth may become an obstacle to seamless connectivity and quality of signals aired, when a large number of mobile devices simultaneously demand network connectivity.
- When multiple users try to use the network simultaneously, for example, on events like new year´s eve, networks are jammed or unable to offer connectivity due to bandwidth constraints.



0 Comments
Please don't Add spam links,
if you want backlinks from my blog contact me on rakeshmgs.in@gmail.com